Network blind spots are the things you can’t see and don’t know about. They’re dangerous. Just like the blind spots on your car, network blind spots can set you up for deadly crashes. Problems will seem to “come out of nowhere” and hit unexpectedly.
Network blind spots create all kinds of serious problems. A major network crash is one. But other problems can pile up too. If you’re operating blind, you’re creating these kinds of network management headaches for yourself:
- Outages and downtime
- Network performance issues
- Incomplete and inaccurate network documentation
- Security issues
- A constant cycle of reactive firefighting
Network blind spots spell trouble for your ability to do your job.
Luckily, there are solutions. When you drive a car, you use mirrors and shoulder checks to make sure issues in your blind spots don’t cause trouble. In a similar way, the right tools and processes on the network can improve your vision and help you avoid a pileup.
This blog post highlights six of the most common network blind spots and how Auvik can help you avoid them. Stay safe out there!
1. Incomplete and inaccurate network documentation
Sending a technician on-site to map the network can take hours, days, or even weeks. After all that work tracing wires and drawing maps, there’s no guarantee that you know about everything that’s on the network.
With just one site, manually tracking every device that’s added, removed, or moved on the network is already a logistical nightmare. If you’re managing multiple sites at a time, it’s impossible. And since your network drawing is static, as soon as something changes, your documentation is automatically out of date and you’ve lost what little visibility you had.
Visibility solution
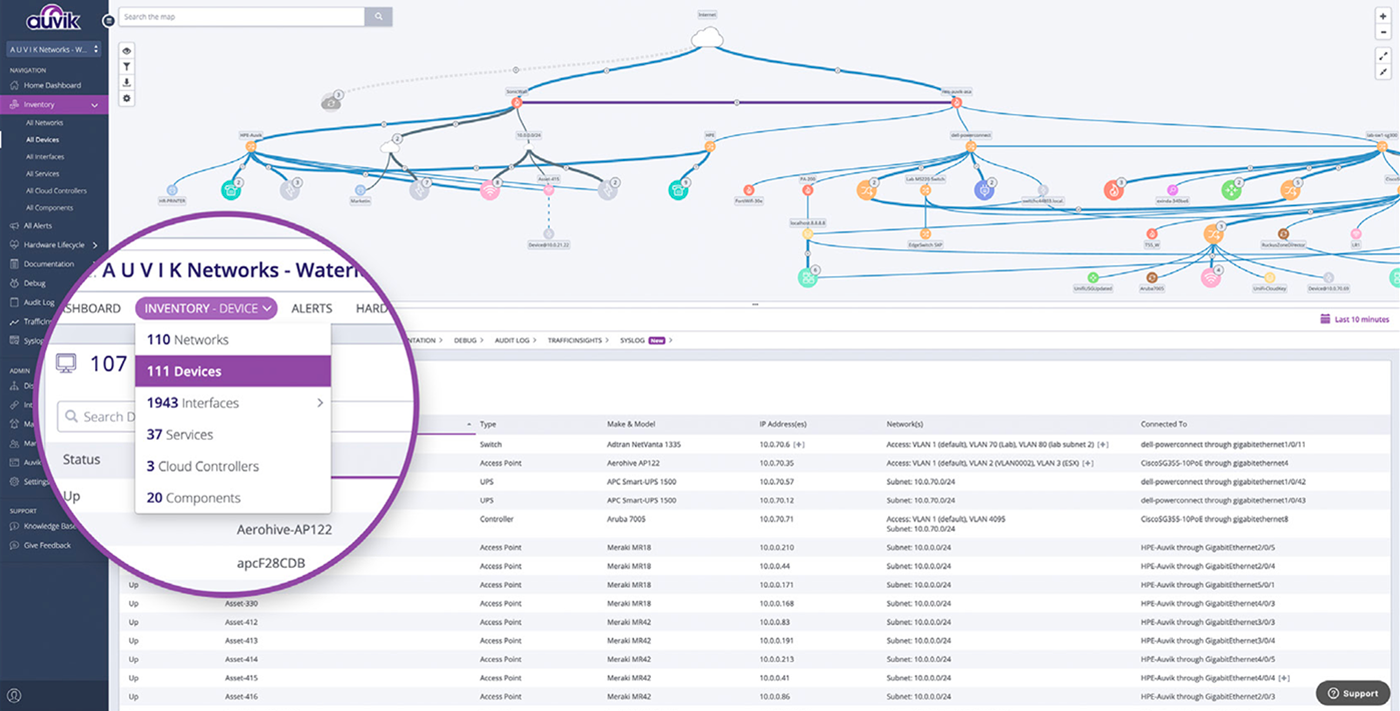
Auvik’s automated inventory uses network protocols to detect and capture full details for every device on the network including make and model, serial number, IP address, and the physical switchport the device is connected to.
Auvik also pulls data from sources like CDP, LLDP, and forwarding tables to meticulously model the Layer 1 network diagram. Layers 2 and 3 are built from ARP tables, IP assignments, and VLAN associations to show you exactly what’s on the network, where it is, and how it’s connected.
“Onboarding used to be an extra couple weeks spent on-site, pulling cables. Now, once we load the Auvik agent, it brings back everything we need, giving us an accurate, real-time view of the network. Now we spend our time focusing on better serving our customers’ networks because we’re not spending time documenting.”
Corey Kirkendoll of 5K Technical Services
2. Unknown and unauthorized devices
An old switch you decommissioned five years ago but never took off the network. A personal smartphone connected to your internal Wi-FI. Regular old LED light bulbs swapped out for their smart counterparts.
We probably don’t need to tell you that shadow IT is a huge issue. The portability of devices like smartphones and tablets, and the rapid growth of IoT devices, more and more end users are adding unknown devices to the networks you manage without telling you. In addition to causing network management headaches like unexpected performance issues, shadow IT presents another attack vector. Gartner estimates that by 2020, a third of successful cyberattacks will be on shadow IT resources.
Visibility solution
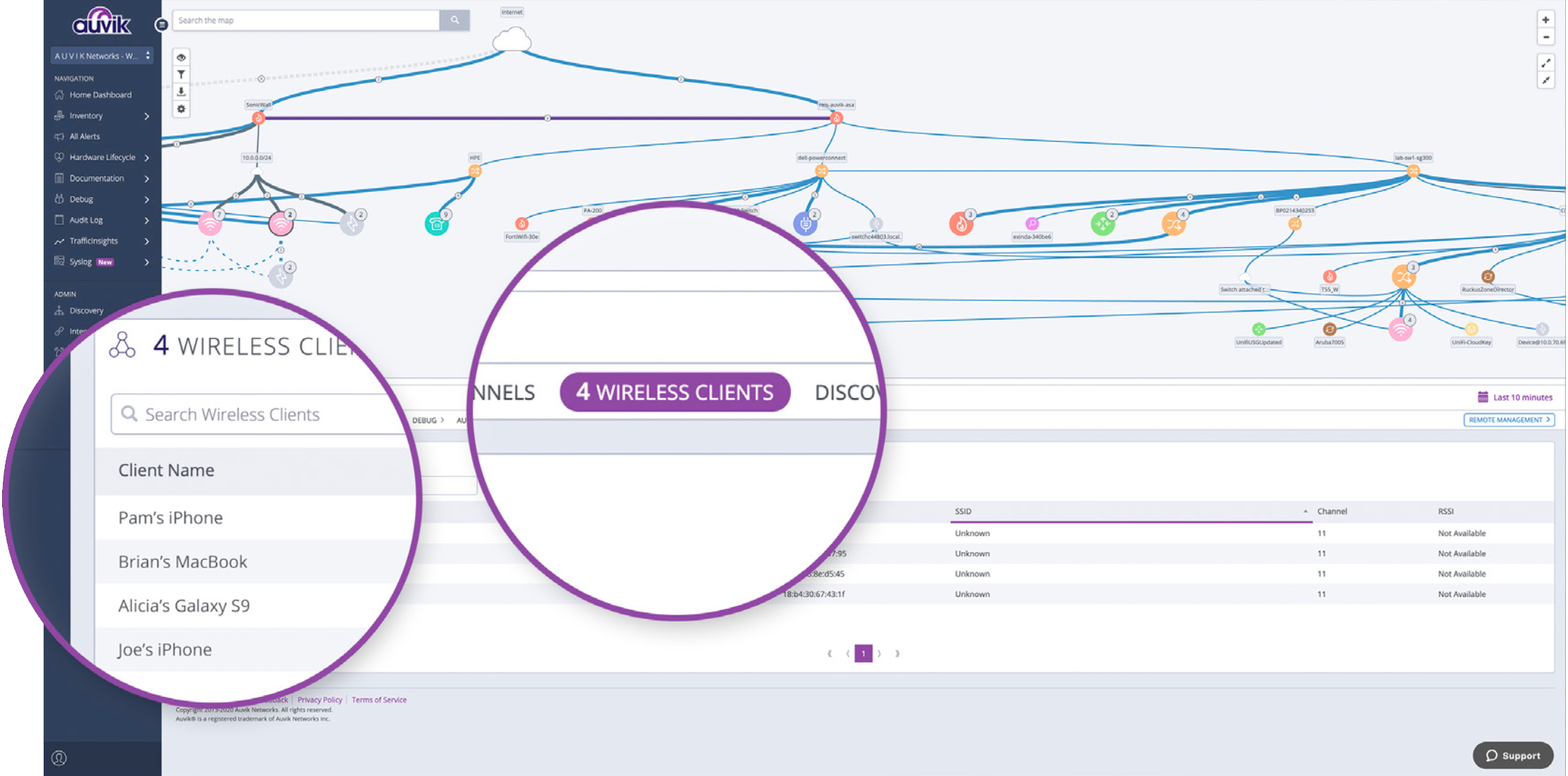
Auvik works out of the box with any device that supports SNMP, CLI, REST APIs, cloud APIs, and more, meaning it’s compatible with over 15,000 network device types from more than 700 vendors.
Auvik’s automated discovery and mapping show you every device on a network—even the ones your users don’t tell you about—and it updates in real-time as the network evolves. From the network map, you’ll see every device you’re dealing with at any given second.
“When it comes to network devices, there’s a lot that can be hidden. We didn’t have a good way to feel comfortable we’d found everything until we started using Auvik.”
Lucas Messina, Practice Group Leader at Kraft Kennedy
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.
3. Not knowing how devices are currently configured
Since manual configuration backups for network devices are extremely time-consuming, you might do them monthly, quarterly, or in some cases, not at all. In fact, a recent report shows that a third of IT pros say they know very little about how their organization’s network is configured and half say their configurations change daily or several times a week.
Without knowing exactly how network devices are configured, you’ll be completely blind to misconfigurations. And should a network device crash, you’ll be left in the dark trying to recreate entire configurations from scratch while your end users wait for you to get them back online.
Visibility solution
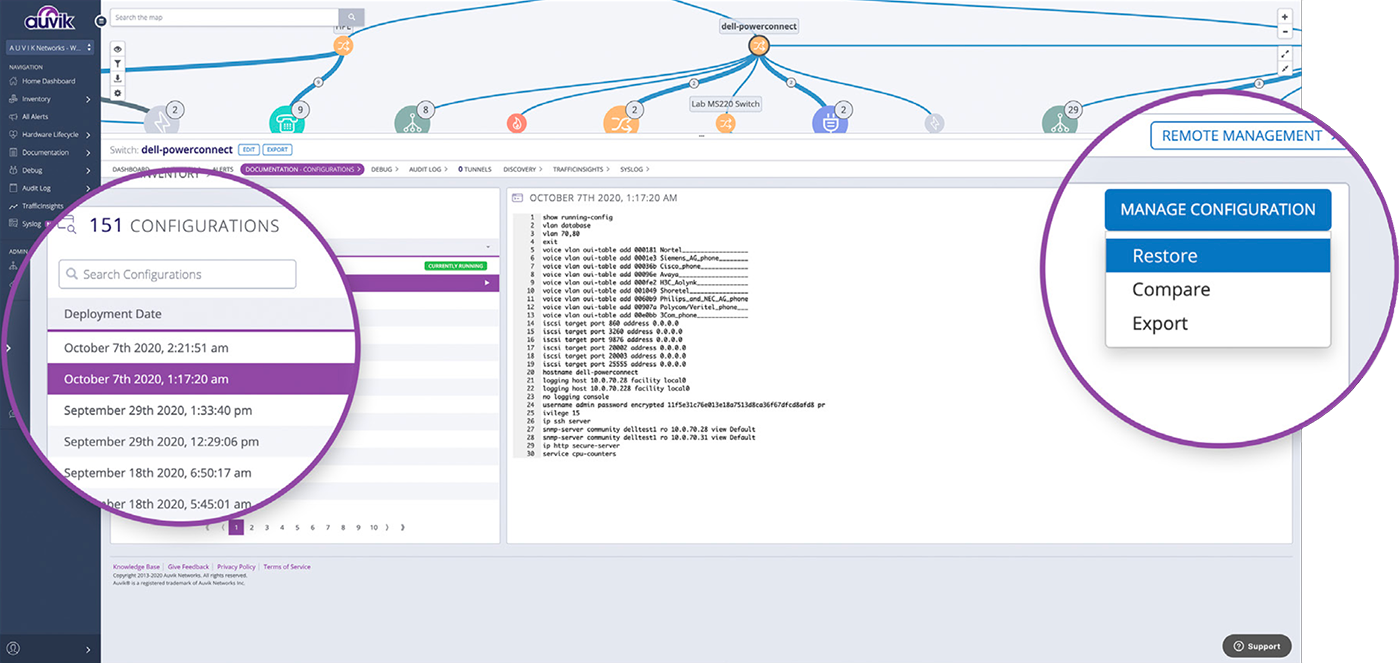
With Auvik, configuration backups are automated. Auvik scans network devices for configuration changes every 60 minutes. If the running config has been altered, the latest config is automatically backed up and the old config gets logged into a version index that’s always available for you to take a look through.
When a network device dies or fat fingers make a mistake changing a device configuration, you won’t have to figure out what went wrong while your users fume without service.
Simply hit Auvik’s configuration restore button to instantly bring things back to the way they were. Alternatively, export the config and apply it to a new device.
“The ease of documentation, troubleshooting, and device management has made our lives much easier. Not only are we able to monitor our networks with ease, but we can also visually see them.”
Will Lee, President of PNC IT
4. Relying on the CLI as your primary data source
Oh, the command-line interface. It’s a powerful tool in many respects but one that’s remained largely untouched despite decades of improvements in usability and design. And for many, it’s their only visibility into what’s happening on the network.
When you’re stuck with the CLI as your only source of network information, it’s easy to get sucked deeper and deeper into a black hole while manually querying individual devices, trying to make sense of the flood of information that flows back.
And unless all of your techs—including the novice ones—are experts in scripting commands and syntax, it’s a challenge to make sense of it all without hours on Google and in forums. (Not to mention how time-consuming that is.) It’s like taking a shot in the dark.
Visibility solution
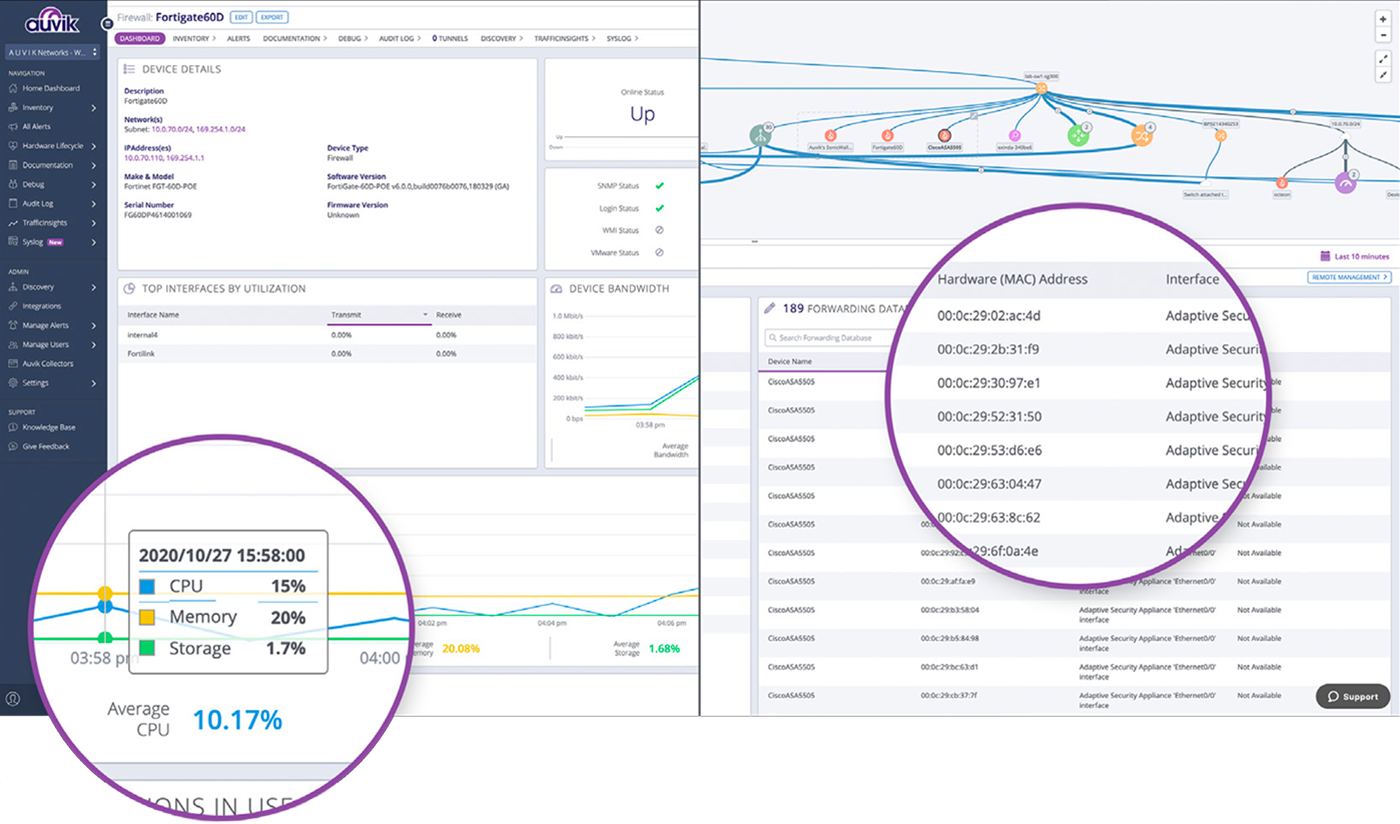
Auvik’s graphical user interface queries the CLI and other data sources for you, then analyzes the data and presents it visually in easily digestible charts and tables so you can see what’s happening on the network without needing deep expertise or tons of time.
Auvik can be used by anyone—it doesn’t matter if you’re an experienced network engineer or you’re just starting out in your networking career. There’s no steep learning curve and you don’t need to be a product expert to know when something goes wrong.
“Auvik is a great network tool that gives you the ability to have a visual representation of a client’s network in real-time that you can interact with.”
Crystal Sharpe of Next I.T.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.

5. No visibility into network traffic
The biggest risk you face is not being able to answer a user’s question. “I don’t know” hurts their confidence and trust in you as their trusted network advisor. “I don’t know” weakens the relationship. And yet, “I don’t know” is an answer that many IT pros must currently give to one of the most common questions of all: Why is my internet slow?
Without detailed traffic reports from the data available through protocols like NetFlow, you have no insight into what’s going on in your network, making it nearly impossible to pinpoint network troublemakers.
Visibility solution
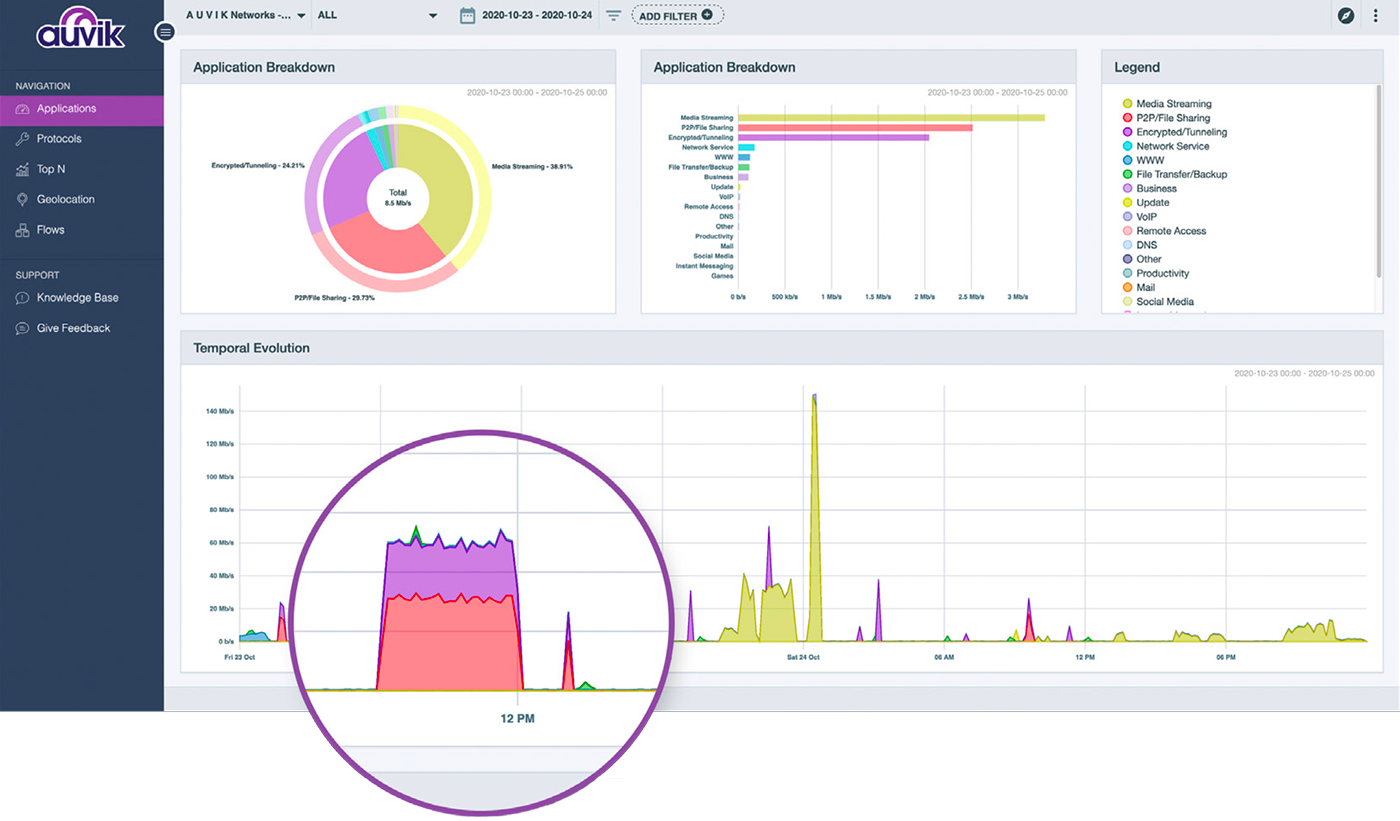
Auvik’s network traffic analysis feature uses machine learning to complement device flow data with additional metadata—like source and destination geography—to give you granular insight into the applications and protocols being used so you can really understand the traffic.
TrafficInsights can collect and analyze flow data from any device supporting NetFlow v5 or v9, IPFIX, sFlow, or J-Flow. If any traffic flows through a TrafficInsights-enabled network device, then you can see who’s on the network, what they’re doing, and where their traffic is going.
“We were able to identify traffic from an application that would have caused over usage of a circuit and ultimately our cloud services production. TrafficInsights gave us the visibility we needed to shape the traffic and avoid a service issue.”
Devon Stephens of Net3 Technology, Inc.
6. No access to device logs
Whether you’re trying to troubleshoot a problem, defend against attacks, or optimize a network environment, event logs are your best source of information.
But logs are stored locally in device memory and unless you’re regularly checking for device logs, you’re blind to potential network issues that are brewing. If a device reboots, all of its logs are gone and you’re stuck playing a guessing game about what went wrong.
Visibility solution
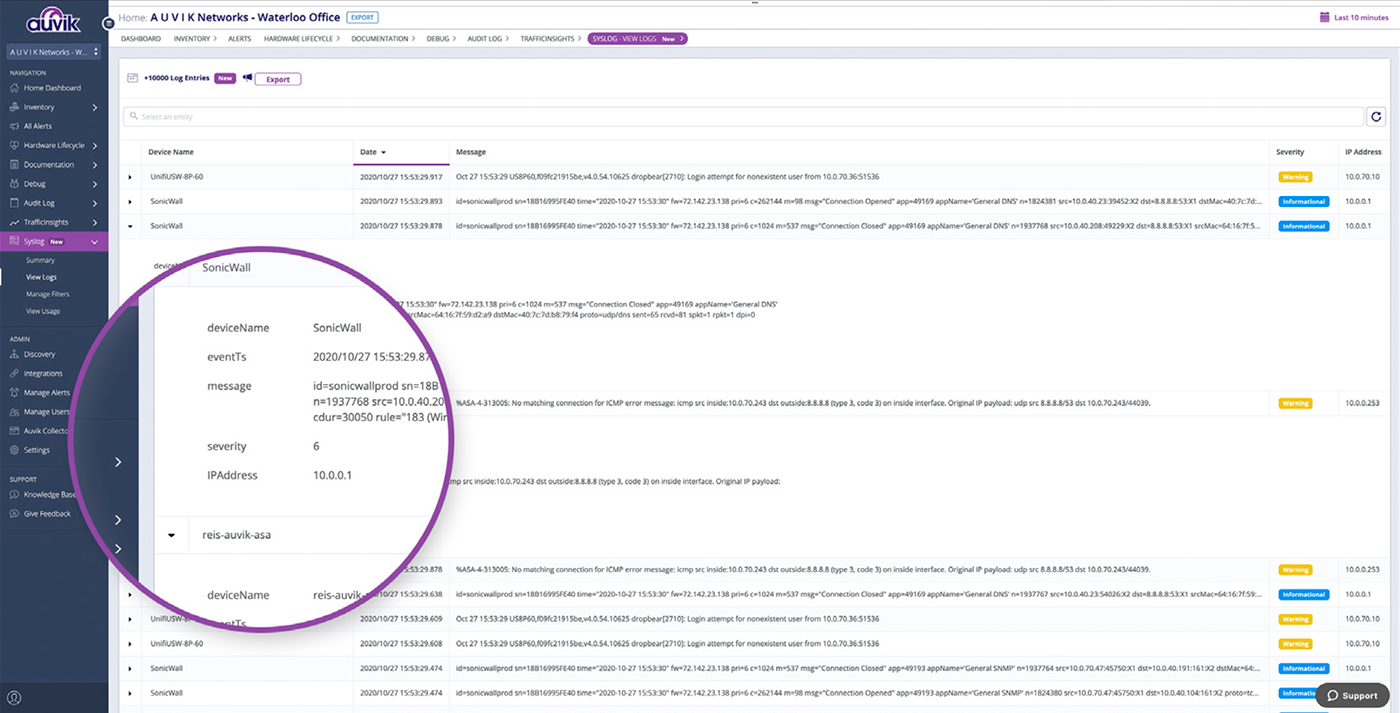
Auvik centralizes log data for all your network devices across all your sites, allowing you to view, search, and filter all of the logs to get to the root cause of network issues.
With Syslog in Auvik, you don’t have to worry about missing important logs pointing to a potential network issue or log into different devices to make sense of the patchwork information you find. Instead, you get all the information you need all in one place.
“The fact that we can log into Auvik, and not have to log into 8 or 20 different network devices to look through logs, makes troubleshooting so much faster and easier. On spanning tree issues, for example, we can see really quickly which port is causing spanning tree to freak out.”
Justin Gallagher, Engineer at Ashton Technology Solutions

Network blind spots white paper
Rogue devices are just one of the common blind spots on a network. In this white paper we outline the other five and how you can avoid them.


