At the beginning of October, conveniently dubbed National Cybersecurity Awareness Month, the Auvik team descended on the city of Pittsburgh to attend Continuum Navigate East 2019.
With recent MSP-targeted ransomware attacks fresh in the minds of all attendees, cybersecurity took the event by storm—from keynotes to casual conversations, there was no escaping it.
What was everyone saying? We put together a list of four key takeaways from the event to fill you in.
1) The rise in cybercrime isn’t ending anytime soon
In fact, in his opening keynote, Continuum CEO Michael George labeled the rise of ransomware attacks on the MSP industry a “pandemic crisis.”
And he’s not the only person who thinks so. On the Ecosystem panel discussion with other managed services vendor executives, Stephan Tallent, Fortinet’s Senior Director of MSSPs, predicted an uptick in MSPs being targeted by threat actors.
Why? “That’s where the money is.”
Stephan says while it may take more time and effort to breach an MSP’s network, it’s a high return on investment for an attacker: Once an MSP is breached, the attacker has access to the MSP’s entire client base, where they can extort even more money from their victims.
2) SMBs are unsuspecting prey
While MSPs understand they’re prime attack targets, their clients aren’t as concerned.
Daniel Eliot, Director of Education and Strategic Initiatives at the National Cyber Security Alliance (NCSA), says it’s because small- to mid-sized businesses (SMBs) don’t believe they’re likely to be targeted by cyberattackers.
During his Small Business, Big Target keynote, he shared some alarming statistics:
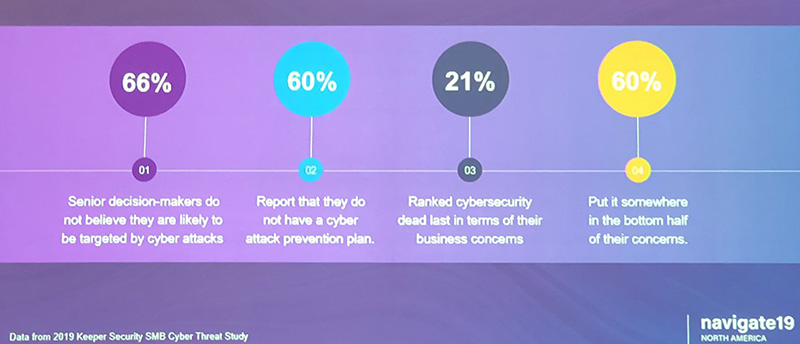
Let that sink in: Two in three SMB decision-makers think they’re safe from cyberattack, and three in five don’t have a cyberattack prevention plan in place. If you’ve been having trouble selling your clients on cybersecurity, this is why.
3) Email is your biggest enemy
While we think we’re immune to phishing attempts, that’s not always the case. Even though the days of the Nigerian prince are long gone (although he’s still active), phishing is still alive and well.
In fact, Daniel shared a scary stat that says otherwise: Over 90% of security breaches happen through email. All it takes is one employee accidentally logging into a website that looks like the company payroll website to take down the network.
As an MSP, Daniel says, you’re responsible for preventing those breaches. But the good news is: A little education can go a long way in the fight against phishing.
4) Use industry best practices to secure your client networks
During the Ecosystem panel discussion, Intermedia COO and CRO Jonathan McCormick said fulfilling the first three steps of the CIS (Center for Internet Security) Cybersecurity Controls framework would be a huge boost to an MSP’s cybersecurity defense.
He then challenged the audience to fulfill the first three steps before the end of the year.
It was a convenient, completely uncoordinated lead in to Auvik’s You Can’t Protect What You Can’t See: Network Security Through Visibility breakout session, where our CMO Jacqui Murphy explained how MSPs can use Auvik to fulfill five steps of the CIS framework.
If you missed Jacqui’s talk but are up to Jonathan’s challenge, here’s how Auvik can help:
- Maintain an up-to-date inventory of all hardware assets. With Auvik, you can see which devices are connected to your client’s network, including details like make and model, serial number, and IP address, as soon as they’re added.
- Analyze for vulnerabilities in the network. If a bug in a device’s software or firmware goes unnoticed, it creates a huge vulnerability and leaves a device open to manipulation. Auvik identifies the current software and firmware version of every device it discovers, so you can quickly see which version it’s running.
- Keep an eye on network ports and protocols. Which devices are connected to which ports? Are only approved ports and protocols being used? If something seems suspicious, Auvik TrafficInsights™ can show you the who, what, and where of the network traffic.
- Harden network device credentials and configurations. If your clients’ login credentials and SNMP strings are left unchanged from the device defaults, a hacker can just look up the default password for a device’s configuration header and get full access. So get creative with your device passwords, put in validated credentials, and set up devices with SSH. Auvik will automatically authenticate you when you log in to the system.
- Make sure you can recover network device configurations. If your client experiences a cyberattack, you need to quickly be able to reset their system and its devices to the most recent configurations before the attack. With automatic configuration backups, Auvik makes it easier than ever to get your clients back up and running.
To test Auvik’s remote management features for yourself, sign up for a free 14-day trial and get full access to your network from the comfort of your desk.
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.