Powerful Configuration Management Software
Streamline network configurations with hourly automated backups, instant change visibility, and robust audit trails.
OR
Loved by customers in independent reviews
Capabilities that streamline change management, compliance, auditing, and device configuration
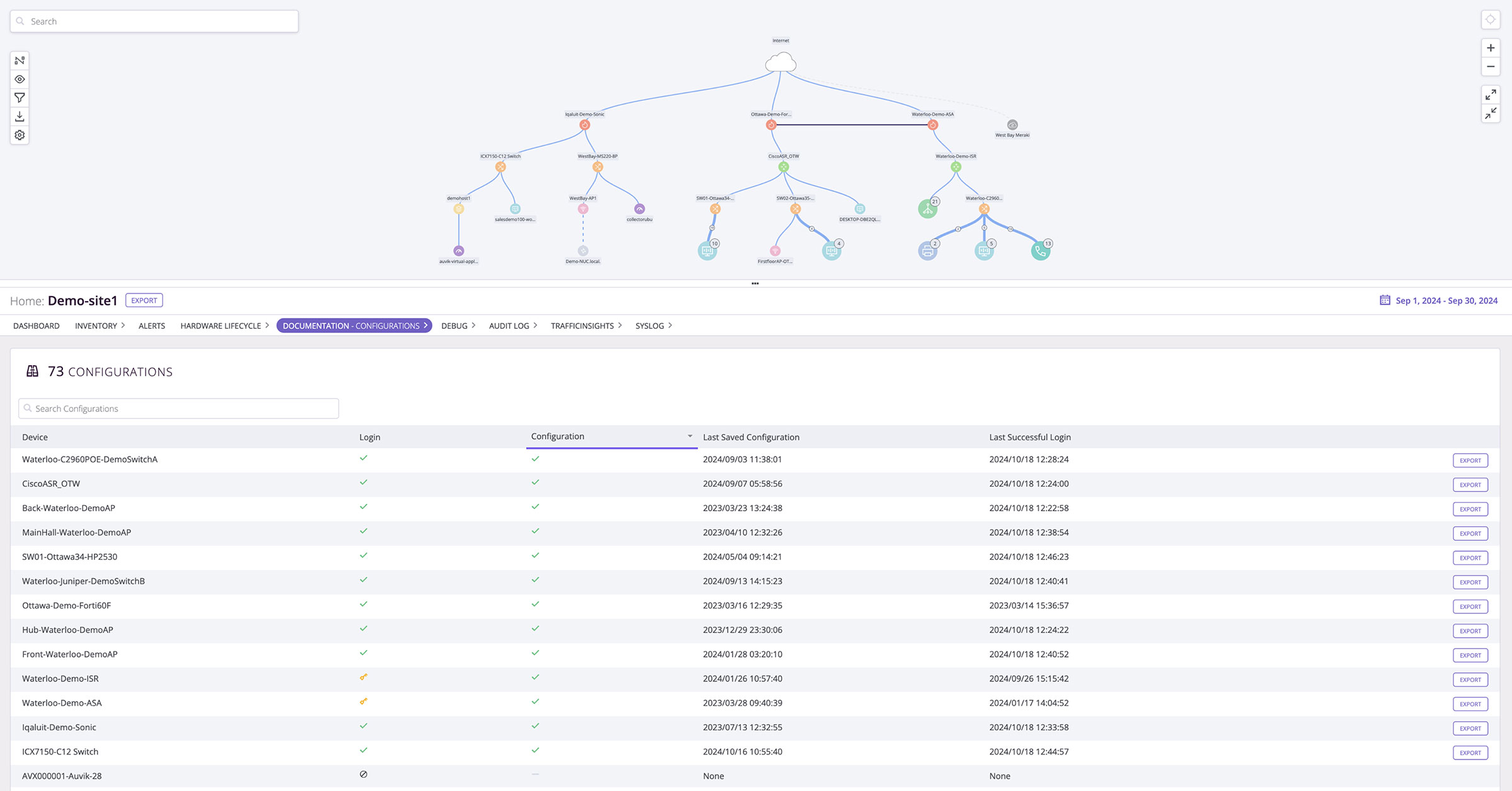
Automated Configuration Compare and Change Management
Instantly see every change made to device configurations. Auvik’s network configuration and change management software instantly compares any two versions to highlight changes, additions, and removals. Automatically track changes over time so you never lose track of your config history again.
Centralized End-User Device Management
Centralize control over all end-user devices. With our network configuration management software, pushing policies and changes across your entire infrastructure is a breeze. Auvik helps you maintain consistent security protocols and software versions while reducing the effort needed for end-user device administration.
Robust Compliance and Auditing
Keep a seamless record of all network changes with automatic tracking and time-stamping for a clear audit trail. Auvik’s network configuration management solution provides your team with continuous visibility into who made changes and when ensuring compliance every step of the way.
Configuration management tailored to your team
Auvik’s configuration management software fits seamlessly into your team’s workflow, making life easier by customizing alerts, automating backups, tracking changes, and simplifying audits to meet your team’s needs. Effortlessly maintain consistency and compliance across devices without manual effort.
For MSPs
Efficiently manage network configuration compliance for all your clients from a single dashboard, ensuring consistency and simplifying compliance. Automated configuration backups let you quickly roll back changes if issues arise, reducing downtime for your clients. With our robust auditing capabilities, you can easily provide reports showing the security and stability of your clients’ network configurations over time. By automating tedious configuration tasks, Auvik frees up your team’s time to focus on higher-value work, allowing you to better serve your clients and expand your service offerings.
For Corporate IT teams
Consolidate network configuration control into one intuitive platform with Auvik, enabling your team to quickly identify and resolve issues before they affect end users. Enjoy automated configuration backups and comparisons for efficient change tracking and simplified compliance audits. Our robust switch and router configuration tools help you streamline tasks that once required tedious manual effort. With Auvik’s configuration management software, your IT team gains the resources needed for a proactive approach, leading to improved uptime and performance.
Benefits of configuration management
Improved visibility
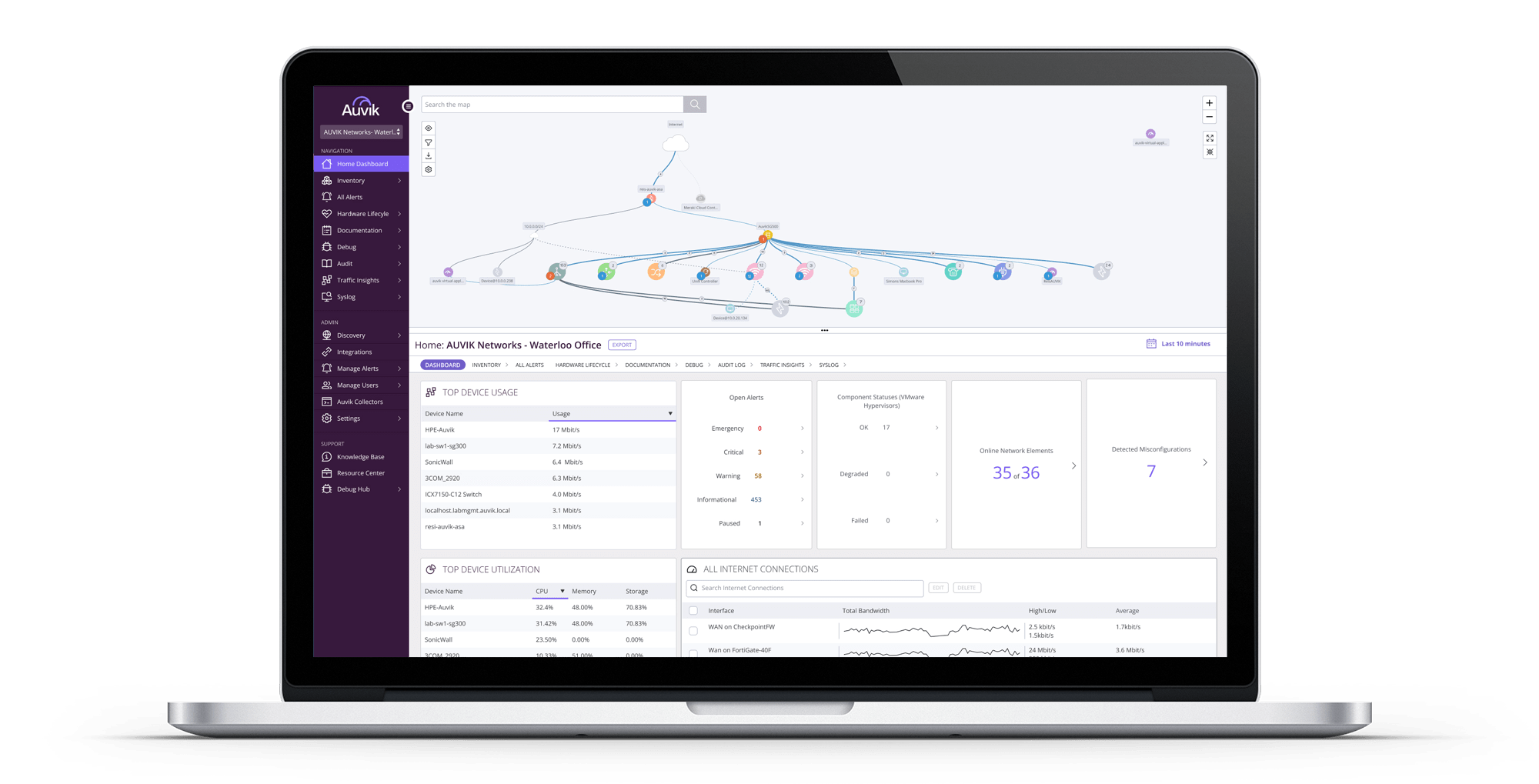
With Auvik’s network management software, you gain a complete view of all devices and connections within your infrastructure to easily track changes, maintain updated documentation, and ensure compliance. This total configuration visibility ensures you can proactively identify risks and optimize performance.
Reduced workload
Save time by automating repetitive configuration tasks. With our automated backups and comparisons of device configurations, you can avoid tedious manual reviews. With centralized change tracking, our configuration management software ensures compliance and removes labor-intensive audits. This robust automation streamlines IT processes, allowing your team to focus on more meaningful work instead of manual busy work.
Streamlined configuration tracking
Efficiently track all device configuration changes over time. Auvik automatically backs up device configs every 60 minutes, so you have an up-to-date version history. Simply compare any two configurations to immediately see changes, additions, or removals in an easy color-coded view — saving your team time by eliminating the need for manual config tracking.
Comprehensive network audit trails
See a complete version history of every change made to device configurations, allowing for thorough compliance auditing and simplifying the process of reverting changes or troubleshooting issues. With complete audit trails, you can ensure proper controls, security policies, and change management processes are followed across your entire network infrastructure.
Easier disaster recovery
Configuration backups make disaster recovery a breeze. Auvik automatically backs up device configurations every 60 minutes, so you can quickly identify issues when mistakes occur. Plus, easily view configuration changes over time and compare any two configuration versions to see precisely what was changed, added, or removed. With up-to-date configs readily available, you can quickly restore devices to the last known good state if disaster strikes.

Auvik pricing
Make network management a breeze with Auvik. Say goodbye to manual tasks with automated inventory, custom alerts, and a single dashboard for all your sites.
- Unlimited users, network sites, endpoints, & support
- Automated network discovery, mapping & inventory
- Network monitoring & alerting
- Configuration management & backup
- Remote device management
- Global dashboards
- APIs & integrations to ticketing, documentation, dashboarding & other third-party tools
Get a Quote
Configuration Management FAQs
What is configuration management?
Configuration management tracks details and changes made to your network devices, providing an accurate record of your current setup. It maintains version histories of device configs and details like IPs, models, locations, and connections. With configuration management, you can easily understand what devices are where and how they’re configured.
What are configuration management tools?
Configuration management tools automatically backup device configs on a set schedule. They compare config versions to reveal specific changes made over time. Additionally, these tools also centralize network details like devices, IPs, models, locations, connections, and lifecycles into searchable, up-to-date documentation.
Why is configuration management important?
Without configuration management, managing network changes becomes chaotic. Details may get scattered across spreadsheets, sticky notes, tribal knowledge, and individual memories, leading to confusion. Configuration management centralizes network data so everyone has access to accurate and up-to-date documentation.
How does configuration management help with compliance?
Configuration management aids in proving compliance by maintaining detailed histories of all network changes. It tracks who made changes, what was changed, and when changes occurred across all devices. This audit trail can demonstrate that configurations adhere to policies around access, security, and architecture.