Break out your buzzword bingo cards, it’s time to talk about SASE or Secure Access Service Edge. Pronounced “sassy,” SASE has become one of the hottest topics in networking and security over the last three years.
Here, we’ll help you filter out the noise and provide a SASE crash course geared toward the networking pro that cares about the practical implications of SASE for IT.
What is SASE?
SASE is a framework that converges network security and WAN services into a holistic cloud-native platform.
Gartner introduced the idea of SASE in 2019 with their “The Future of Network Security Is in the Cloud” research paper. Instead of a bunch of discrete appliances and cloud services to implement WAN connectivity and security, converge them all in a single platform. Make that platform cloud-based, and emphasize granular identity-based security.
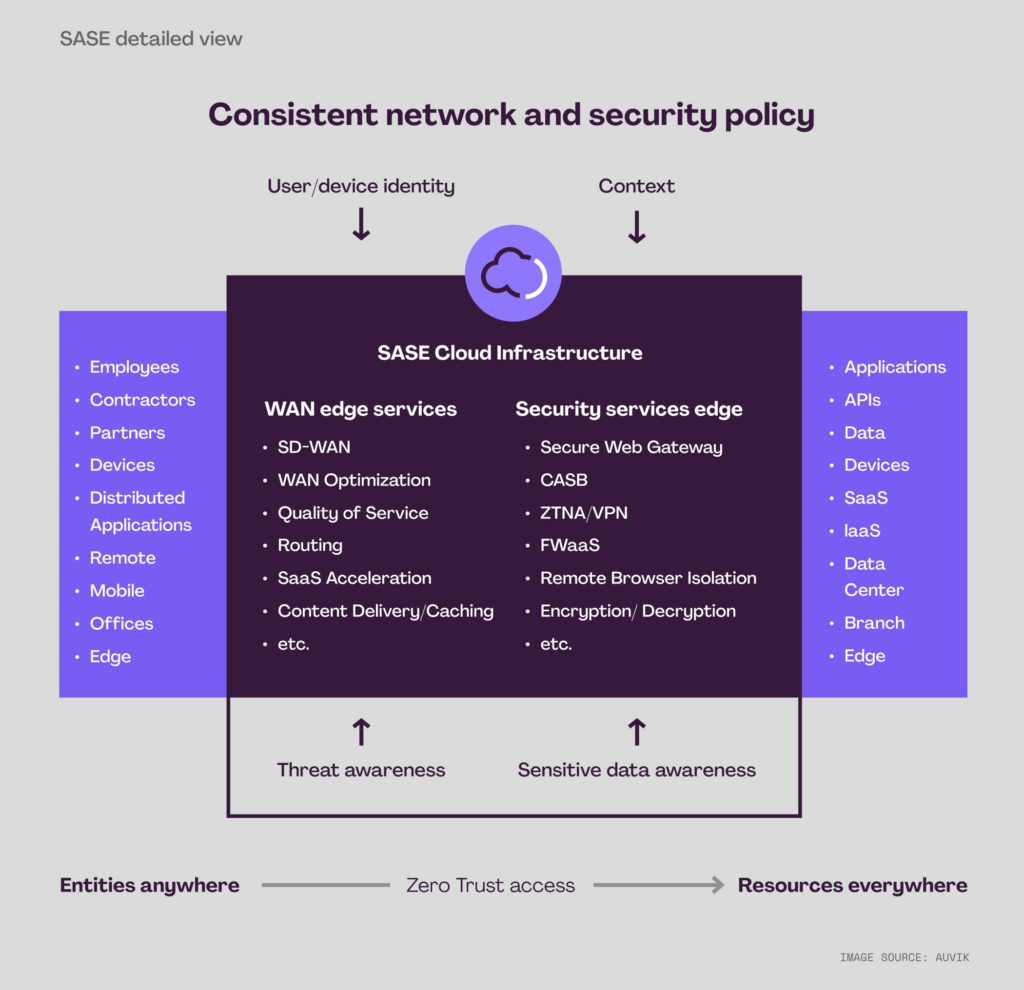
The promise of SASE is that it provides connectivity for all of an organization’s resources and entities using granular, contextually-aware security while reducing implementation complexity and tool sprawl. More for less.
Gartner also made it clear that how the services are delivered matters. SASE is about converging capabilities, so simple service chaining (linking discrete virtual machines to provide services) isn’t enough. Services should be built-in into a single platform to provide a more seamless experience. Otherwise, SASE wouldn’t be anything different than using SD-WAN and security platforms together.
Core SASE capabilities
Today, there are plenty of platforms from vendors like Cisco, VMware, CloudFlare, and Zscaler labeled SASE. Many marketing materials also call out why one platform is SASE and others aren’t. Because SASE is such a broad term, it can be hard to say who’s right and wrong.
Fortunately, Gartner does maintain a list of core, recommended, and optional SASE capabilities. Below are the core SASE capabilities as of Gartner’s 2022 Strategic Roadmap for SASE Convergence:
- SD-WAN
- Cloud access security broker (CASB)
- Zero-trust network access (ZTNA)
- Secure Web Gateway (SWG)
- Firewall as a service (FWaaS) with IDS/IPS
- Line rate operation
- Sensitive data and malware inspection
What’s the SASE standard?
In IT, answering “what is X?” authoritatively usually begins and ends with an IEEE standard or IETF RFC. But when it comes to SASE, there isn’t one. At least not yet. Gartner does a good job of providing high-level guidance, but it isn’t the same thing as a well-defined technical standard.
MEF helps us solve this problem with the SASE Services Framework. That framework provides a way to tighten up terminology around SASE and ensure we’re not talking past each other.
Unfortunately, not all the players in the SASE market have adopted SASE definitions, and true standardization is still a work in progress. The overall confusion is such a big issue that it was a key point of discussion by the MEF Technology Advisory Board at MEF’s 2022 annual meeting.
Pros and cons of SASE
If SASE can deliver on its promise, it can provide real business benefits. A single platform that provides the flexibility and scalability of SD-WAN, with zero-trust network security, can streamline IT operations and greatly reduce tool sprawl while solving performance and security challenges.
On the other hand, the market is still maturing. Most platforms aren’t delivering the full promise of SASE yet. Frankly, the market hasn’t completely aligned on what is and isn’t SASE. Additionally, SASE is inherently cloud-native, which comes with all the traditional cloud vs. on-prem tradeoffs. For enterprises where compliance and data sovereignty matter, centering your security on a cloud platform could be a non-starter.
Are all the other buzzwords just part of SASE?
SASE is a collection of services and capabilities, and the other buzzwords are a subset of those services and capabilities. Let’s take a look at how SASE compares to other popular IT buzzwords. As we go, remember that these components can be delivered as part of a SASE implementation or on their own.
SD-WAN
You can have SD-WAN without SASE, but you can’t have SASE without SD-WAN. SD-WAN was the big WAN buzzword pre-SASE, and many SD-WAN vendors are now SASE vendors. SD-WAN offers functions like routing, QoS, dynamic path selection, link aggregation, and load balancing and can be deployed using cloud or appliance-based models.
In overly simplistic terms, SD-WAN is the network side of SASE. That means SASE couples the network abstraction and optimization of SD-WAN with security services.
CASB
A cloud access security broker (CASB) sits between users and cloud services and allows IT to implement security controls on public cloud resources. With a CASB, organizations can use services like single sign-on (SSO), device profiling, audit logging, and threat detection to harden their public cloud infrastructure. CASB can be delivered as its own security measure, or as part of an overall SSE convergence (see below).
ZTNA
Zero trust network access (ZTNA)—sometimes called software-defined perimeter (SDP) — is a security model that requires explicit verification of trust. Zero trust helps organizations implement tighter security controls and more granular permissions than the traditional “castle-and-moat” style security, where anything that made it past the firewall was trusted implicitly.
With ZTNA, app access is decoupled from network access. This helps limit lateral movement in the event of a breach and enforces the principle of least privilege. There are multiple ways to implement ZTNA, but generally, it involves a broker or controller that enforces security policies.
In the SASE framework, ZTNA provides a foundation for granular security and access control.
SSE
Security Service Edge (SSE) is another popular security buzzword from Gartner. Fortunately, this buzzword has a pretty straightforward meaning. It’s the security half of SASE. Remote browser isolation, ZTNA, CASB, FWaaS, and SWG fall into this category. While those capabilities can all be delivered separately, SSE converges them.
What does SASE mean for the future of VPN?
Based on Gartner’s Strategic Roadmap, a “lower priority” 3-5 year goal enterprises should have is to eliminate 95% of network-level VPN access. And it’s just one of several potential VPN alternatives. With that in mind, it’s natural to question the future of traditional internet-based VPN protocols for site-to-site connections or remote access in organizations.
VPN has plenty of flaws, but it’s probably not going away for a while. VPN usage increased during the COVID-19 pandemic, and “traditional” VPN is likely to have a long tail because it’s so ingrained in many implementations and is often still the right tool for the job. Gartner even lists “legacy VPN” as an optional capability, which indicates that IPsec and SSL tunnels still have a place in IT for some time to come.
That said, the VPN landscape is evolving, and IT should expect solutions like SASE—or one of its components like SD-WAN—to pop up where VPN once would have.
Even if another buzzword replaces SASE in the years to come, familiarity with the underlying concepts will help IT make informed decisions and look past the marketing buzz. While SASE can help you do away with many on-prem appliances, they’re still a big part of modern networks. If you’re looking to make a network-related purchase in the near future, be sure to check out the Auvik network device buying guide first!
Whether it’s a SASE future or a long hold for VPN, Auvik can help your team with astonishing speed and ease. Ready to see what real network visibility and monitoring look like?
Your Guide to Selling Managed Network Services
Get templates for network assessment reports, presentations, pricing & more—designed just for MSPs.